You’re sitting at your desk when your phone rings. It appears to be your boss—or at least, it sounds just like them. They urgently ask you to process a wire transfer or reset login credentials for an executive account. The voice is calm, convincing, and familiar. But there’s just one problem—it’s not your boss. It’s an AI-generated deepfake, part of a growing cyber threat called voice phishing or vishing.
In this article, we’ll explore how vishing works, why it’s rising so rapidly, and what you can do to protect yourself in the era of voice-based AI attacks.
What Is Voice Phishing (Vishing)?
Vishing involves manipulating victims over the phone to extract confidential data, steal money, or trigger illicit actions. Unlike traditional phishing, which uses emails or text messages, vishing adds the power of verbal persuasion—now enhanced with artificial intelligence.
The AI Deepfake Twist
AI voice cloning is made possible by advanced text-to-speech models trained on a person’s speech samples. With just a few seconds of recorded audio—scraped from YouTube, TikTok, or voicemail—attackers can generate a digital copy of someone’s voice. These voice models are then used to create synthetic audio that mimics the target’s tone, cadence, and even emotional cues.
Today’s deepfake voices are so realistic that even cybersecurity experts have been fooled in controlled tests. As Cybersecurity Dive reports, the FBI has issued warnings about impersonation threats targeting U.S. officials using AI-generated voices.
Why Is This Trend Accelerating?
Voice phishing powered by AI isn’t just a future concern—it’s already here. Several factors contribute to its rapid growth:
- Accessibility of tools: Voice cloning tools are available online, often for free or with minimal cost.
- Remote work culture: The pandemic normalized voice-only communication, making verification harder.
- Hard to detect: AI-generated voices often sound so real that most people can’t tell the difference.
- Social engineering: Emotional manipulation is easier when delivered by a trusted voice.
Examples Making Headlines
In one alarming case, a Hong Kong bank manager transferred $35 million after receiving instructions in a cloned voice believed to be his superior. Similar incidents have occurred in the UK, Germany, and the United States, highlighting the global nature of this threat.
Introducing ASRJam and EchoGuard
Fortunately, researchers aren’t standing still. Two promising technologies have emerged to counter AI-powered vishing: ASRJam and EchoGuard.
ASRJam: Fighting AI with Audio Confusion
ASRJam is a defensive tool that works by injecting audio signals that confuse automatic speech recognition (ASR) systems. It creates adversarial noise patterns that humans don’t notice but AI transcription tools can’t interpret correctly. This “jam” breaks the communication pipeline for vishing bots and reduces their effectiveness.
The key advantage? Human conversations remain intelligible while malicious AI systems get scrambled responses. It’s a practical defense for call centers, banking hotlines, and customer service channels.
EchoGuard: Detecting Synthetic Voices
EchoGuard is a different kind of solution—it analyzes vocal echoes and waveform patterns to detect signs of AI synthesis. It acts as a filter for phone calls, flagging or blocking calls that exhibit traits of deepfake audio. While still in early trials, it shows promise for enterprise applications and mobile phone integration.
Psychology of Voice-Based Attacks
Why are these scams so effective at tricking people? It comes down to two key psychological principles:
- Authority bias: We’re trained to obey voices we associate with authority, such as managers, police, or family members.
- Emotional urgency: Many vishing calls simulate crises—”your bank account is under attack” or “your child is in danger”—to force immediate action.
Combining these triggers with a familiar voice creates a powerful manipulation tool that few can resist in the moment.
How to Protect Yourself and Your Business
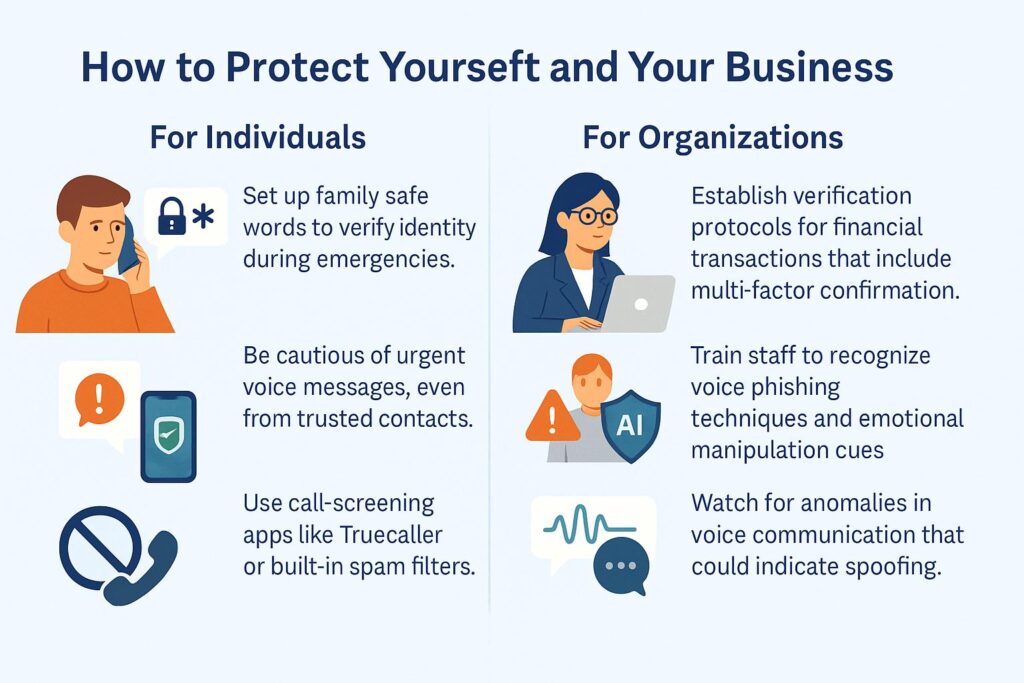
For Individuals
- Set up family safe words to verify identity during emergencies.
- Be cautious of urgent voice messages, even from trusted contacts.
- Use call-screening apps like Truecaller or built-in spam filters.
- When unsure, always hang up and reconnect using a number you know is real.
For Organizations
- Establish verification protocols for financial transactions that include multi-factor confirmation.
- Train staff to recognize voice phishing techniques and emotional manipulation cues.
- Implement AI detection tools in help desks and client-facing departments.
- Watch for anomalies in voice communication that could indicate spoofing.
Legal and Ethical Challenges
As this technology advances, governments are struggling to keep up. Some states in the U.S. have introduced laws requiring disclosure when AI is used in robocalls or impersonations. However, enforcement remains limited, and global cooperation is still evolving.
At the same time, legitimate uses of AI voice generation—such as accessibility tools, gaming, and customer service—must be protected. Balancing rapid innovation with robust security has become one of this decade’s biggest challenges.
The Future of Voice Authentication
Adding sound-based ‘AI tags’ or digital watermarks to generated audio content. But as voice cloning grows, so does the risk of misuse. Moving forward, the focus will likely shift toward multi-modal authentication that includes biometrics, behavioral patterns, and contextual data.
We may also see new industries emerge—think of them as “deepfake firewalls”—that protect communication channels in real time, much like antivirus software for audio.
Deepfake Voice in Pop Culture and Media
Interestingly, AI-generated voices are not only seen in cybersecurity threats but also in pop culture and entertainment. From movie dubbing and video game characters to AI-generated music covers on TikTok, the ability to replicate voices is rapidly entering mainstream media. While these uses may seem harmless or even fun, they also normalize deepfake audio and can blur the line between fiction and reality.
This dual-use nature of AI voice tools—both creative and malicious—makes it harder to regulate and more critical to educate the public about its implications. If we can clone Morgan Freeman’s voice to narrate bedtime stories, what’s stopping a cybercriminal from doing the same to commit fraud?
Corporate Responsibility in the Age of AI
As AI-driven scams rise, companies developing voice cloning tools must implement ethical frameworks and guardrails. Tech firms can play a key role by:
- Embedding watermarking or audible “AI tags” into generated voice content.
- Restricting use cases to verified and approved industries.
- Requiring identity verification before using voice cloning services.
- Providing transparency reports on how their tools are used and audited.
Several startups are already stepping up by building ethical voice synthesis platforms with built-in consent tools. Still, as with any powerful technology, it’s a race between responsible innovation and malicious exploitation.
Red Flags: How to Spot a Vishing Attempt

Spotting a vishing call can be tricky—especially when the voice sounds familiar. Here are some warning signs that can help you identify a potential AI-generated scam:
- Urgent requests: Claims of emergencies, deadlines, or crises demanding immediate action.
- Pressure to bypass protocol: Asking you to skip standard verification processes or not document the request.
- Calls outside normal hours: Scammers often call early in the morning, late at night, or during holidays.
- Inconsistent details: A deepfake might reveal itself through awkward pronunciations, mismatched context, or unnatural language.
- Refusal to switch channels: If a caller resists verifying the request via email or video, it could be suspicious.
Training yourself and your team to recognize these red flags can greatly reduce the risk of falling victim to a vishing attack.
Global Response: How Governments Are Reacting
Governments around the world are beginning to recognize the threat posed by AI voice cloning. While some countries have passed laws requiring AI disclosures in robocalls, most legislation remains reactive and fragmented. Here’s a look at what’s being done:
- United States: The FCC has ruled that AI-generated robocalls are illegal under the Telephone Consumer Protection Act.
- European Union: The proposed AI Act includes provisions for watermarking and responsible deployment of synthetic media.
- China: Enacted laws requiring consent and identification for deepfake audio or video use.
Despite these steps, enforcement lags behind technology. A global framework or cybersecurity treaty may be necessary to effectively govern misuse across borders.
Educational Outreach: Fighting Back Through Awareness
Beyond technical solutions and legislation, education plays a vital role in combating vishing. Public awareness campaigns, workplace training modules, and school cybersecurity programs are essential. Platforms like ByteToLife.com can contribute by making cybersecurity knowledge accessible, actionable, and easy to understand.
When more people know how these scams work and what to watch for, attackers lose their edge. Prevention is still the most powerful tool in cybersecurity.
Frequently Asked Questions (FAQ)
Conclusion
AI-powered voice phishing represents one of the most urgent cybersecurity challenges of our time. It combines technical innovation with psychological manipulation, creating a threat that’s both sophisticated and deeply human.
But with awareness, proactive security measures, and advanced defense technologies like ASRJam and EchoGuard, we can outpace attackers and build a safer digital world.
Want to Learn More?
Explore more AI and cybersecurity guides from ByteToLife:
- AI Voice Phishing and Deepfake Vishing Guide
- Prompt Injection: A Cybersecurity Threat in the Age of AI
- State-Sponsored Smartphone Attacks and How to Protect Yourself
Stay sharp, stay curious, and share this knowledge to help others stay safe in the AI age.



