Imagine a world where cybercriminals can spin up an authentic-looking phishing site in just 30 seconds. That world isn’t hypothetical anymore. Thanks to generative AI platforms like Vercel’s v0, it’s now a disturbing reality. In mid-2025, cybersecurity experts reported how attackers cloned entire login pages—like those of Okta or Microsoft 365—using simple AI prompts.
In this article, we explore how these platforms are being exploited, the risks it poses for businesses and individuals, and most importantly, what we can do to defend against this new threat.
🔍 What Is Generative AI for Web Design?
Generative AI tools like v0, Wix’s AI builder, or Framer AI let users create fully designed websites from a single prompt. Instead of hand-coding or using templates, you simply type “Build me a login page that looks like Okta’s” — and it delivers. Fast.
Features that make it powerful (and dangerous):
- Rapid generation (< 60 seconds)
- Minimal technical skill required
- Clean, responsive designs
- Hosting on trusted domains (like vercel.app)
While originally created to empower developers and designers, these tools are now being abused by threat actors with malicious intent.
🚨 Real Example: The 30-Second Phishing Clone
In a now-viral case highlighted by Axios Future of Cybersecurity, attackers used v0 to replicate the Okta login interface in under 30 seconds. The generated site mimicked font, layout, and structure—enough to fool even trained eyes if delivered via a convincing spear-phishing email.
What’s worse? These pages are hosted on reputable platforms, meaning standard URL red flags (like strange domains or extensions) often don’t apply.
⚙️ How Cybercriminals Exploit This AI Capability
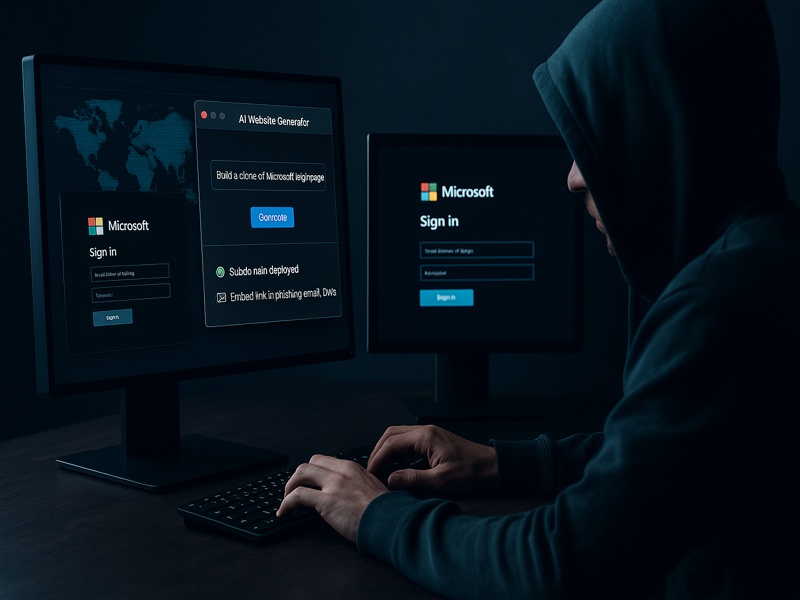
The process is disturbingly simple:
- Open an AI website generator (e.g., v0.dev)
- Input a prompt: “Build a clone of Microsoft login page”
- Deploy instantly to a subdomain
- Embed into phishing campaigns via email, SMS, or social DMs
This turns phishing from an artisanal crime into a mass-producible one.
Targets include:
- Enterprise SSO portals
- Crypto wallets & exchanges
- Cloud platforms (AWS, Google Cloud)
- Online banks
📉 The Cybersecurity Impact
With phishing already responsible for over 36% of breaches, according to the Verizon Data Breach Investigations Report, adding generative AI to the mix increases both volume and believability.
Key challenges for defenders:
- AI-generated pages don’t always trip traditional filters
- Hosting from known services reduces blacklist effectiveness
- Speed of deployment outruns takedown teams
🛡️ Defending Against AI-Powered Phishing Sites
Organizations and users alike need to adopt more robust, AI-aware security practices.
1. Use Passwordless Authentication
Platforms like Okta, Google, and Microsoft are already pushing toward passkeys or biometric sign-in, which render traditional phishing login forms useless.
2. Educate About Generative Threats
Security awareness programs should now include how AI is used to automate phishing and social engineering attacks.
3. Adopt Email & Web Gateway Filtering with AI
Solutions like Proofpoint or Cloudflare Gateway use behavioral analytics to block suspicious content before it reaches the user.
4. Monitor Trusted Platforms
Tools should be set up to detect abuse of popular hosting sites like vercel.app or netlify.app for impersonation campaigns.
5. Encourage Platform Responsibility
AI builders should enforce:
- Prompt filtering (block keywords like “clone X login”)
- Abuse reporting workflows
- Automatic rate limits for mass deployments
⚖️ Policy Implications
This growing threat raises questions about regulation:
- Should AI-generated phishing sites fall under CISA‘s mandatory breach disclosure rules?
- Will low-code platforms be required to vet prompt input?
- What responsibility do AI creators have in stopping abuse?
🔗 Related Articles on ByteToLife
- AI Voice Phishing & Deepfake Threats
- Prompt Injection Attacks: The Hidden AI Threat
- The Rise of AI-Powered Cyberattacks
🧬 The Rise of Intelligent Phishing in the AI Era
Phishing has evolved from crude emails full of typos to professionally designed messages that mirror corporate branding. With generative AI, attackers no longer need to be web developers or designers. They can automate the production of scam websites that are virtually indistinguishable from legitimate ones.
Over the past decade, phishing techniques have included:
- Email spoofing
- Link obfuscation
- Typosquatting domains
- Man-in-the-middle attacks
- Now, AI-generated clone sites
The AI twist dramatically increases scalability, reduces costs for attackers, and introduces new challenges in distinguishing authentic from fake in real time.
🌐 The Role of DNS and Certificate Spoofing
Cybercriminals are also combining AI-generated sites with techniques like DNS spoofing or acquiring TLS certificates via Let’s Encrypt. This makes the phishing page not only look real but also pass HTTPS checks. Seeing the padlock makes people feel safe — but that sense of security can be false.
Preventive actions:
- DNS monitoring and alerts for lookalike domains
- Certificate Transparency logs to detect suspicious certificates
- User education that “padlock” ≠ safe
🤖 Can AI Help Fight AI-Powered Threats?

Absolutely. Just as attackers use AI to craft their tools, defenders are beginning to do the same. AI-driven cybersecurity platforms are evolving to detect behavioral anomalies, page structure similarities, and real-time phishing attempts.
Examples include:
- Darktrace – detects unusual behavior in enterprise traffic
- SentinelOne – autonomous endpoint protection
- Microsoft Sentinel – AI-powered SIEM & threat detection
The key is to integrate AI in a layered defense strategy and ensure human analysts are looped in for high-fidelity alerts.
📊 Case Study: AI Phishing in a Corporate Breach
In April 2025, a North American logistics firm fell victim to an AI-powered phishing campaign. Attackers cloned the company’s HR portal using Vercel’s v0 and sent emails with fake onboarding documents. The site captured employee credentials, leading to lateral movement across departments and eventual ransomware deployment.
Lessons learned:
- AI phishing can bypass traditional web filters
- Credential reuse across internal systems is still a problem
- Timely user reporting helped reduce dwell time
🧭 Strategic Recommendations for CISOs
Chief Information Security Officers (CISOs) must now treat AI phishing as a Tier 1 threat. The following should be part of your 2025 roadmap:
- Continuous phishing simulations — now including AI variants
- Third-party risk assessments for vendors using AI builders
- Zero trust architecture implementation
- Red teaming exercises focused on generative AI attacks
Incorporating these strategies isn’t just proactive — it’s essential for survival in a world where the lines between real and fake are increasingly blurred by machines.
💬 Expert Opinions: What Cybersecurity Leaders Are Saying
Leading voices in cybersecurity are sounding alarms about the unintended consequences of generative AI. Kevin Mandia, CEO of Mandiant, emphasized in a recent panel at RSAC 2025 that “AI lowers the barrier to entry for cybercriminals in ways we’ve never seen. What used to be a long, drawn-out task is now done in a fraction of the time.”
Other experts like CyberArk CTO Udi Mokady argue that the shift requires a new mindset: “Defenders must stop thinking in static defenses and adopt dynamic, adaptive AI defenses that learn in real-time.”
📱 Mobile Phishing & Deepfakes Convergence
Generative phishing isn’t limited to websites. Increasingly, attackers are merging AI-generated landing pages with voice deepfakes or smishing attacks. You receive a realistic text message from ‘Apple Support,’ complete with a deepfake voice call and a cloned login page — all generated by AI.
Combining these elements makes the scam nearly indistinguishable from legitimate contact, especially for less tech-savvy users.
Recommendations:
- Enable call verification via secondary apps
- Use family-safe words for sensitive requests
- Verify urgent calls via different channels
🔍 Future of AI Abuse Detection
The future lies in real-time abuse detection. Just as email providers use spam filters, AI platforms will soon need “misuse filters” — algorithms trained to detect prompts that aim to create malicious outputs.
Platforms like OpenAI and Anthropic are already working on “constitutional AI,” where safety rules are built into the model. For web generators, this could mean refusing prompts that replicate known brand login pages or contain suspicious intent.
📘 Resources for Further Reading
- What Is Ransomware & How to Protect Yourself
- Top Digital Security Tips for 2025
- Cloudflare Phishing Blog
- UK NCSC Phishing Protection Guide
🎯 Key Takeaways
- Generative AI tools like v0 can clone phishing sites in seconds
- These tools are being exploited by cybercriminals at scale
- Traditional detection systems struggle with speed and authenticity
- Zero-trust, AI-driven defense, and prompt filtering are critical
- Real-time detection and AI ethics enforcement will be the next battleground
🌍 Global Perspective: How Different Regions Are Responding
The misuse of generative AI in phishing isn’t just a U.S. concern — it’s global. Countries are taking different approaches in response to the rise of AI-driven cybercrime.
🇪🇺 European Union
The EU is drafting new AI regulations under the AI Act, which includes strict rules on high-risk AI systems. Platforms that could be abused to create phishing content may fall under this regulation, requiring built-in safety mechanisms.
🇸🇬 Singapore
Singapore has developed one of the most robust AI governance frameworks in Asia. The country mandates transparency in AI tools and encourages public-private partnerships to identify abuse patterns.
🇦🇺 Australia
Australia’s eSafety Commission is launching public awareness campaigns to combat AI-enhanced scams, focusing particularly on protecting vulnerable populations like seniors and non-tech users.
These global efforts show a growing recognition that AI phishing isn’t just a technical problem — it’s a policy and education challenge too.
🧠 Frequently Asked Questions
Generative AI phishing involves using AI tools to automatically create realistic phishing websites that mimic login pages, banking portals, or cloud services to trick users into entering sensitive information.
With tools like Vercel’s v0, hackers can clone a login interface in as little as 30 seconds using a simple prompt—no coding required.
They are often hosted on reputable platforms like Vercel or Netlify and closely mimic real brands, making them appear legitimate even to tech-savvy users and bypassing traditional security filters.
Use passwordless logins when possible, enable multi-factor authentication (MFA), avoid clicking unknown links, and verify the authenticity of websites before entering credentials.
AI platform developers should implement prompt filtering, usage rate-limits, and abuse reporting tools to prevent malicious use of their generative systems.
Conclusion
We’re at the frontier of a new era in cybersecurity. As artificial intelligence grows smarter, so do the methods of digital attackers. Defending against these threats requires a collaborative, multi-layered approach — from developers building safeguards into their tools to governments crafting forward-looking regulations and end-users staying informed and vigilant.
Generative AI is here to stay. The question is: will we let it be a weapon, or will we shape it into a shield?
Stay informed. Stay secure. Stay ahead — with ByteToLife.com.